From fire drills to flow: Automating privacy requests in financial services
In this post, we explore why traditional finserv workflows fail, and provide a step-by-step roadmap for moving from reactive compliance fire drills to trusted, scalable data operations.

Every month for financial institutions, millions of people challenge errors on their credit reports, request access to their banking data, or opt out of marketing. For banks and lenders, each of these requests represents much more than typical customer service. These are legally binding obligations that are directly connected to regulators and public perception of the brand. Most organizations still treat requests as ad hoc tickets, handled by high-manual-input, sprawling technological webs. The result is predictable: delays, errors, mounting regulatory risk and a steady erosion of customer trust.
Let’s take a concrete example. In July 2025, the Consumer Financial Protection Bureau fined Equifax $15 million for mishandling hundreds of thousands of credit reporting disputes. Regulators found cases closed without proper investigation, deleted errors reappearing on reports, and coding flaws generating inaccurate credit scores. The case highlights a systemic challenge: financial institutions built on manual or outdated data handling can’t keep up with today’s scale of consumer privacy rights.
In this post, we’ll examine why traditional, manual approaches to privacy request fulfillment break down for financial services. We’ll then look at the limitations of ticket-based workflows, the role of infrastructure-level automation, and how embedding privacy-as-code can transform disputes, corrections and access requests into reliable, real-time processes. Finally we’ll outline a step-by-step roadmap for institutions to move from reactive fire drills to operational integrity — building trust at scale by making privacy a core capability of their data systems.
Reactive compliance can’t keep up with privacy requests
Equifax alone processes about 765,000 credit reporting disputes every month. Each one is a legal request under the Fair Credit Reporting Act and other privacy regulations, requiring verification, correction, and response within 30 days. At that scale, manual investigation can’t keep up. Requests span core banking systems, credit bureaus, cloud providers, and a sprawl of SaaS applications. Each handoff adds delays and risk of error and increases the scale of data complexity. When the process breaks, the cost isn’t just regulatory penalties but further erosion of consumer trust in financial records.
Current workflows fall short
Most financial institutions still handle privacy requests with tools built for the pre-AI era. Requests get logged like IT tickets, routed across siloed teams, and resolved by hand. Or, a software solution manages the first-mile collection of DSARs but can’t handle the fulfillment.
- Ticket-based systems. Service desk software or CRM add-ons create visibility but not enforcement. Staff still pull records manually from banking platforms, credit bureaus, and SaaS tools, leaving too much room for error.
- Workflow portals. Intake portals track “who owns what” but rarely connect to underlying systems. Deletion, correction, and packaging still require manual work, often managed with spreadsheets and email chains.
- In-house tooling. Custom scripts can cover one system or jurisdiction but break as regulations change. They also depend on tribal knowledge. When a developer leaves, compliance logic leaves too.
Infrastructure for finserv privacy
Manual workflows can track requests, but they can’t fulfill them at the speed or precision regulators demand. In financial services, the sustainable model is automation at the infrastructure layer. Privacy-as-code embeds enforcement directly into data systems so disputes, corrections, and access requests are executed in real time with full auditability. Below are the four main infrastructure improvements financial institutions can unlock by using advanced tooling such as that which Ethyca provides.
1. Privacy-as-code automation
Manual casework depends on compliance staff to interpret regulations and push actions through fragmented systems. Privacy-as-code replaces this with codified rules that execute automatically. For example, a correction request will not proceed unless the individual is verified via KYC. A deletion request will automatically check retention requirements before executing. By embedding these rules in code, enforcement becomes consistent, auditable, and jurisdiction-aware.
2. Real-time data discovery
Fulfilling access or dispute requests requires knowing where data resides across banking platforms, credit bureaus, SaaS tools, and vendor integrations. Traditional discovery is interview-based and quickly outdated. Automated discovery maps systems continuously, providing an accurate inventory of where customer records live and how they flow. This eliminates the lag between business changes and governance, and ensures that no system is overlooked during a request.
3. Automated fulfillment
Equifax’s enforcement showed the cost of case-by-case handling: disputes closed without review, deleted errors resurfacing, and flawed code producing inaccurate credit scores. Infrastructure-level automation prevents those failures. Once a correction is applied, system logic blocks it from re-entering. Identity-theft flags stop records from resurfacing. Updates propagate consistently downstream, and every action is logged for audit — creating accuracy for consumers and defensibility for regulators.
4. Integration with compliance operations
Financial services institutions already operate under extensive regulatory frameworks. Privacy automation must integrate with those workflows rather than sit apart from them. Infrastructure-level enforcement connects directly to existing compliance monitoring and reporting systems, producing the evidence regulators expect without duplicating processes. This reduces operational overhead and turns consumer rights fulfillment from an ad hoc burden into a standard component of compliance operations.
Financial institutions that keep treating privacy as a ticketing problem will always be one step behind — chasing disputes, patching errors, and absorbing the cost of lost trust.”Ethyca Team
The business case for data privacy infrastructure
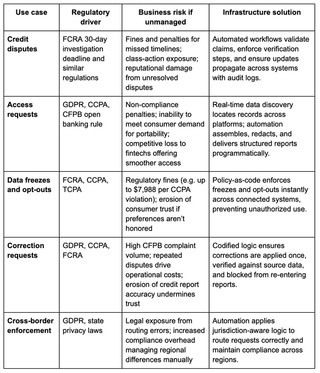
The case for buying privacy infrastructure is grounded in specific, high-volume workflows where manual handling creates unacceptable risk and friction. From credit disputes to cross-border enforcement, each case has a clear business risk and path to automation. The table below breaks down these scenarios, showing how codified logic and real-time enforcement turn compliance obligations into reliable, scalable processes.
Implementing privacy infrastructure for financial services
Institutions can move from reactive casework to automated privacy infrastructure in measured stages. Each step builds a foundation for the next, reducing risk while demonstrating value internally.
Step 1: Audit request volumes and timelines
The first step is establishing a clear baseline. Automated discovery tools can measure how many requests are being received, how long fulfillment takes, and where bottlenecks exist. This turns anecdotal frustration into quantifiable data that can drive investment decisions.
Step 2: Prioritize high-risk workflows
Not every workflow needs to be automated at once. Program managers should focus first on the most frequent or regulator-sensitive processes, such as credit disputes under the FCRA. Targeting high-volume, high-risk requests ensures that early improvements deliver immediate compliance and cost benefits.
Step 3: Embed policy-as-code
Once workflows are identified, the next task is codifying business and regulatory rules directly into data pipelines. This means translating obligations into executable logic: for example, requiring KYC verification before a correction proceeds, or blocking deletion of records that are still within statutory retention.
Step 4: Automate execution
With policies defined, institutions can automate the fulfillment tasks themselves. Redaction, routing across systems, packaging consumer reports, and logging each action can be executed programmatically. This replaces hours of manual casework with consistent, system-level enforcement.
Step 5: Track metrics continuously
Finally, success must be measurable. Metrics such as time-to-fulfill, error rate, and audit readiness should be monitored continuously. These provide evidence for regulators while also giving leadership clear visibility into the operational gains from automation.
The next step: Privacy that powers growth
Manual fulfillment of privacy requests cannot keep pace with the scale and scrutiny of financial services. It leaves institutions exposed to regulatory action and erodes consumer confidence in the accuracy of their financial records. Automating at the infrastructure level transforms compliance from a reactive fire drill into a technical flow that can scale with your business. Institutions that embed privacy-as-code are not only meeting legal obligations, they are building the foundation for durable consumer trust.
Financial institutions that keep treating privacy as a ticketing problem will always be one step behind — chasing disputes, patching errors, and absorbing the cost of lost trust. At Ethyca, we’ve seen how this shift to privacy-as-code turns regulatory exposure into operational resilience with large banks and other financial institutions. If you are ready to move from reactive fire drills to reliable data flows, reach out to speak with our team. We’d love to show you what that journey looks like with our customers.
If your firm is still treating governance as a checkpoint at the finish line, now is the moment to rethink. Book an intro with Ethyca to see how embedded governance can transform your AI development into a true competitive advantage.
About Ethyca: Ethyca is the trusted data layer for enterprise AI, providing unified privacy, governance, and AI oversight infrastructure that enables organizations to confidently scale AI initiatives while maintaining compliance across evolving regulatory landscapes.

.jpeg?rect=270,0,2160,2160&w=320&h=320&fit=min&auto=format)



.png?rect=0,3,4800,3195&w=320&h=213&auto=format)
.png?rect=0,3,4800,3195&w=320&h=213&auto=format)